
Locke Lord QuickStudy: Cyber Attacks Continue to Grow and Evolve
Cyber criminals continue to prey on websites with unpatched vulnerabilities and ill-protected point of sale (POS) systems to steal credentials such as personal data, credit card numbers and bank account details.
Common methods to be aware of
Fraudsters are known to use methods most commonly associated with their victim’s normal business practices - wire transfers in most cases, cheques in others. Intrusions are facilitated through a phishing scam in which a victim receives an email from a seemingly legitimate source that contains a malicious link. When the victim clicks on the link, it downloads malware, allowing the criminals unrestricted access to data, including passwords or financial account information.
Fraudsters also contact companies by email or phone pretending to be lawyers or representatives of law firms claiming to handle confidential or time-sensitive matters. Organizations and Internet users should be vigilant in strengthening their guard against the anticipated surge in cyber attacks targeting web servers, POS systems and mobile devices.
It is predicted that extortion via DDoS (distributed denial-of-service) and Ransomware will also flourish as cyber criminals are increasingly offering paid ransomware services (complete with kits for attacks on different operating systems) and managing ransom payments.
Prevention
|
Computer Crimes Ordinance in Hong Kong
The main piece of legislation in Hong Kong which has been introduced against computer related crime is the Computer Crimes Ordinance. Enacted in 1993, it has, through amending the Telecommunications Ordinance (Cap. 106), Crimes Ordinance (Cap. 200) and Theft Ordinance (Cap. 210), created some new offences and broadened the coverage of existing offences, as follows:
Related Crimes - Hong Kong
| Law | Provisions | Maximum Penalty |
| Telecommunications Ordinance S.27A, Cap. 106 |
By telecommunications, obtains unauthorized access to any computer | Fine of $25,000 |
| Crimes Ordinance S.59, Cap. 200 |
Extending the meaning of property to include any program or data held in a computer or in computer storage medium | Not applicable |
| Crimes Ordinance S.59 and 60, Cap.200 |
Extending the meaning of criminal damage to property to misuse of a computer program or data | 10 years' imprisonment |
| Crimes Ordinance S.85, Cap. 200 |
Extending the meaning of making false entry in bank book to falsification of the books of account kept at any bank in electronic means | Life imprisonment |
| Crimes Ordinance S.161, Cap. 200 |
Extending the meaning of making false entry in bank book to falsification of the books of account kept at any bank in electronic means |
5 years' imprisonment |
| Theft Ordinance S. 11, Cap. 210 |
Extending the meaning of burglary to include unlawfully causing a computer to function other than as it has been established and altering, erasing or adding any computer program or data | 14 years' imprisonment |
| Theft Ordinance S. 19, Cap. 210 |
Extending the meaning of false accounting to include destroying, defacing, concealing or falsifying records kept by computer |
10 years' imprisonment |
Source: www.infosec.gov.hk/english/ordinances/corresponding.html
Computer crime in Hong Kong
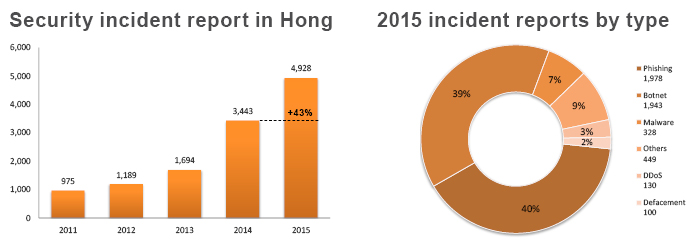
The Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT) handled 4,928 security incident reports in 2015, up 43% from 2014. Phishing (1,978 cases) powered the surge, with an increase of 233%, as a result of new “flash” phishing attacks (1,375 cases, or 69% among phishing) that were launched using local web hosting services as cover. Incidents relating to mobile devices also rose by 86% to 286 cases.
BEC Scams in the United States - US$798 million and counting
Business E-mail Compromise (BEC) scams continue to grow and evolve targeting businesses of all sizes. The FBI’s Internet Crime Complaint Center (IC3) reported a 270 percent increase in identified victims and exposed loss since January 2015. The scam has been reported in all 50 states and in 79 countries. Fraudulent wire transfers were sent to 72 countries, with the majority of transfers going to Asian banks located in China and Hong Kong.
The IC3 reports that from October 2013 to August 2015, BEC scams claimed 8,179 individual victims (7,066 in the U.S. and 1,113 non-U.S.) with a total exposed loss of US$798,897,959.25. Similar incidents identified by international law enforcement agencies during the same period bring the BEC exposed loss to over US$1.2 billion.
Read our previous QuickStudy on Wire Transfer Fraud for practical advice for organizations and individuals as to the steps to take for recovery of stolen funds. Time is of the essence.
For more information on the matters discussed in this Locke Lord QuickStudy, please contact the authors.
Don't miss a beat.
Sign up for our newsletter and get the latest to your inbox.

